Be careful :
Comodo Internet Security PRO

Comodo Internet Security 5.5.195786
Comodo claim that their firewall is unique in that it passes all known leak tests to ensure the integrity of data entering and exiting your system. Comodo has put firewall through all kinds of sophisticated tests to ensure its firewall powerful enough to ward off these attacks with default settings. No other firewall has had to work this hard.
Features:-
-
Secures against internal and external attacks
-
Blocks internet access to malicious Trojan programs
-
Safeguards your Personal data against theft
-
Delivers total end-point security for Personal Computers and Networks
 Download Download
HiJackThis
Trend Micro HijackThis is a free utility that generates an in depth report of registry and file settings from your computer. HijackThis makes no separation between safe and unsafe settings in its scan results giving you the ability to selectively remove items from your machine. In addition to this scan and remove capability HijackThis comes with several tools useful in manually removing malware from a computer.
HijackThis inspects your computers browser and operating system settings to generate a log file of the current state of your computer. Using HijackThis you can selectively remove unwanted settings and files from your computer. Because the settings identified in a HijackThis log file can belong to both legitimate software and unwanted malware, it is important to use extreme caution when choosing to removing anything using HijackThis.
HijackThis also comes with a process manager, HOSTS file editor, and alternate data stream scann
 Download Download
CCleaner
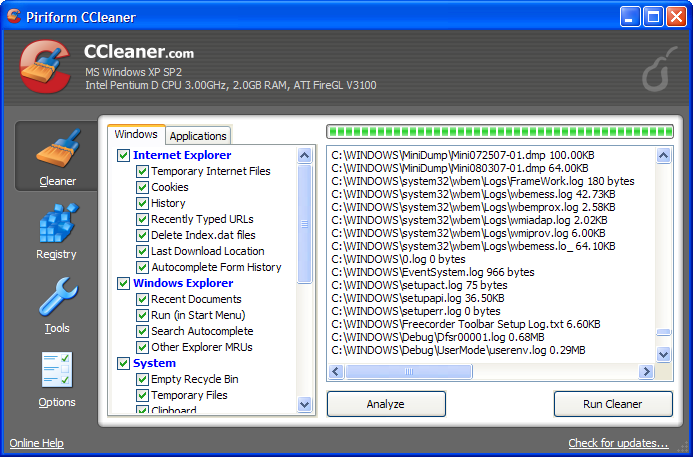
CCleaner is a freeware system optimization, privacy and cleaning tool. It removes unused files from your system - allowing Windows to run faster and freeing up
valuable hard disk space. It also cleans traces of your online activities such as your Internet history. Additionally it contains a fully featured registry cleaner. But the
best part is that it's fast (normally taking less than a second to run) and contains NO Spyware or Adware! :)
 Download Download
Process Explorer
ProcessExplorer for keeping an eye on the files and directories open by any process.
 Download Download
VeraCrypt : Open Source Free Encryption
It adds enhanced security to the algorithms used for system and partitions encryption making it immune to new developments in brute-force attacks.
This is acceptable to the legitimate owner but it makes it much more harder for an attacker to gain access to the encrypted data.
VeraCrypt storage format is INCOMPATIBLE with TrueCrypt storage format. Hidden volume (steganography) and hidden operating system.
 Download Download
|
